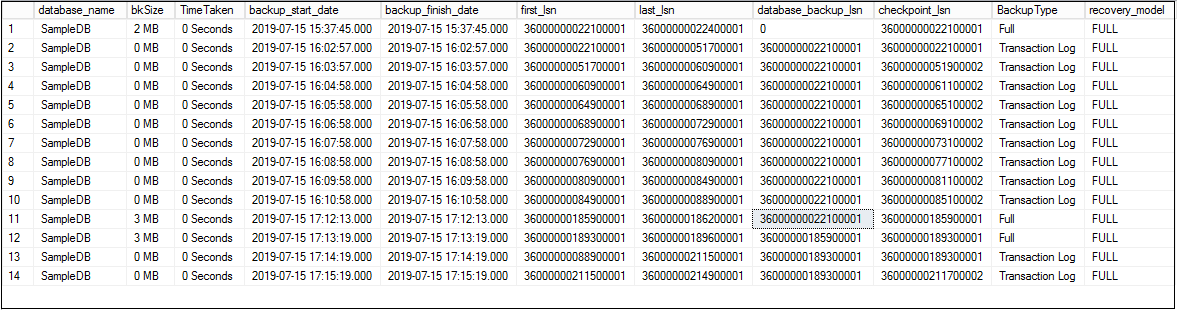
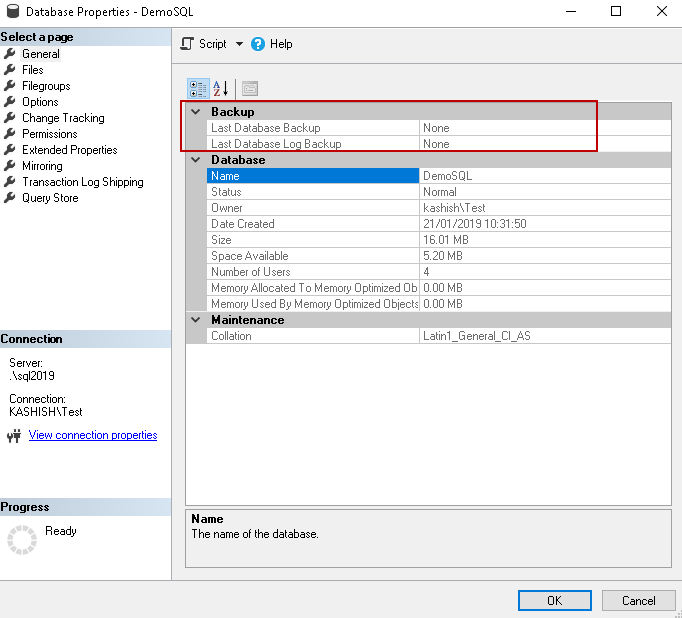
Understanding Log Sequence Numbers for SQL Server Transaction Log
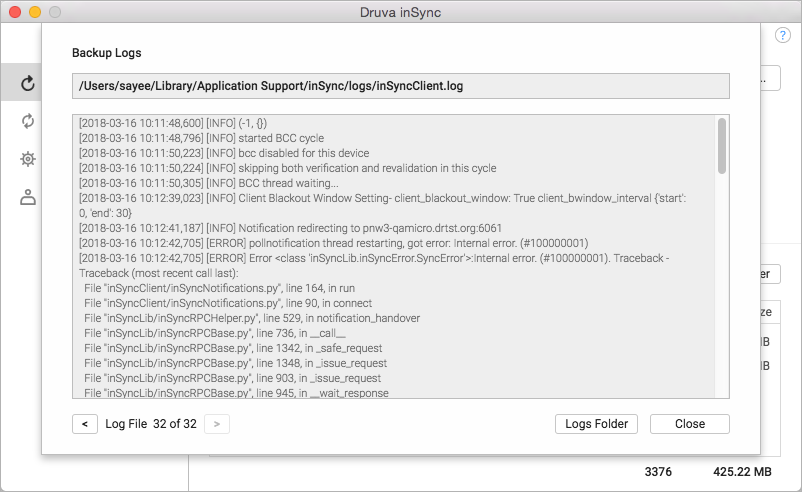
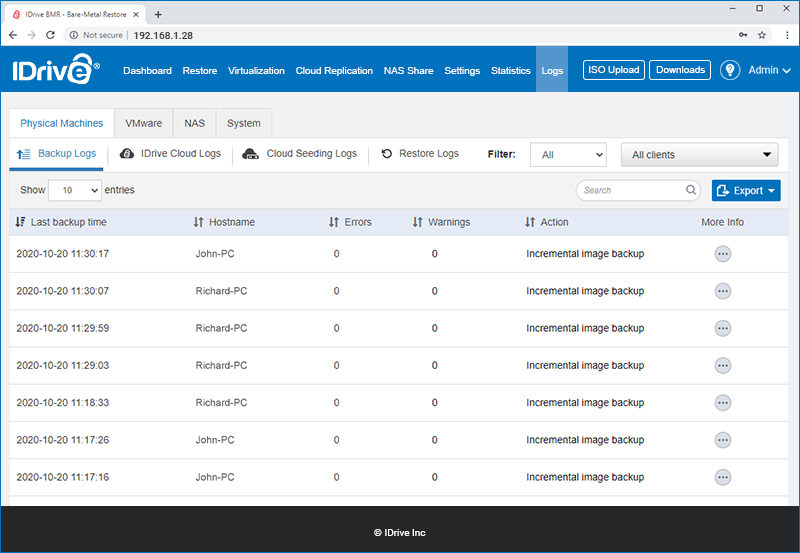
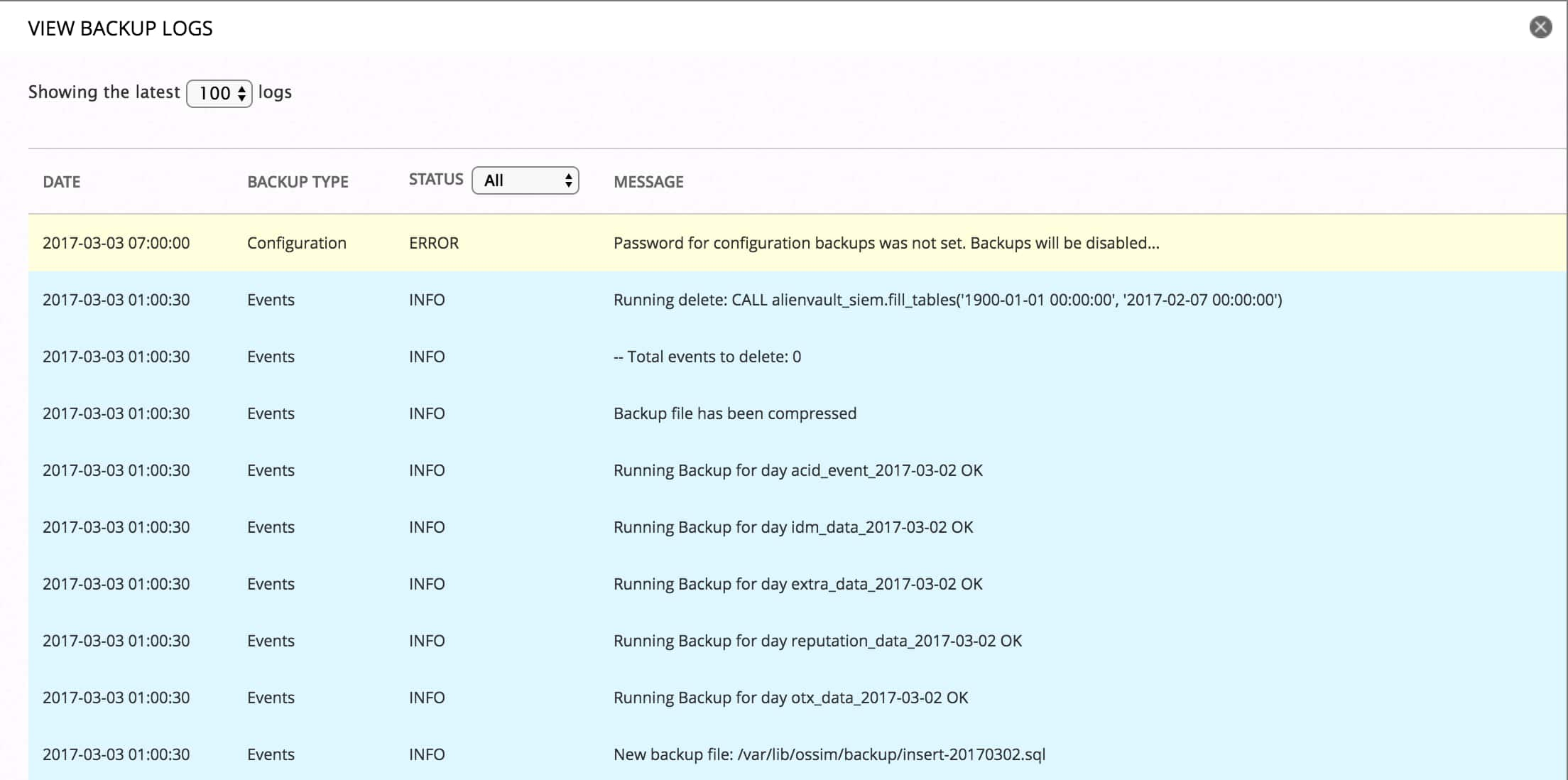
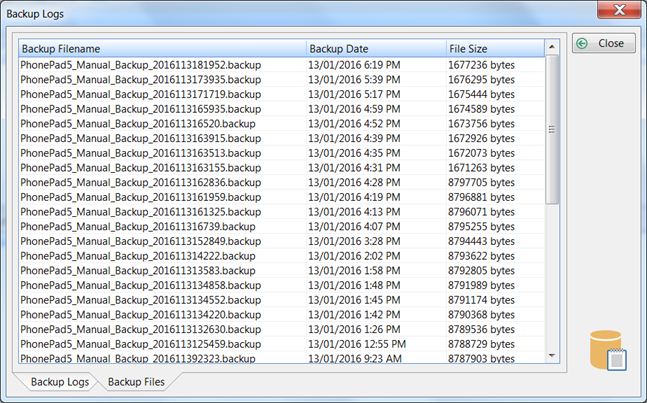
View backup and restore logs Druva Documentation
Best amp Simple Backup Options Prevent Data Loss Smartly Computer
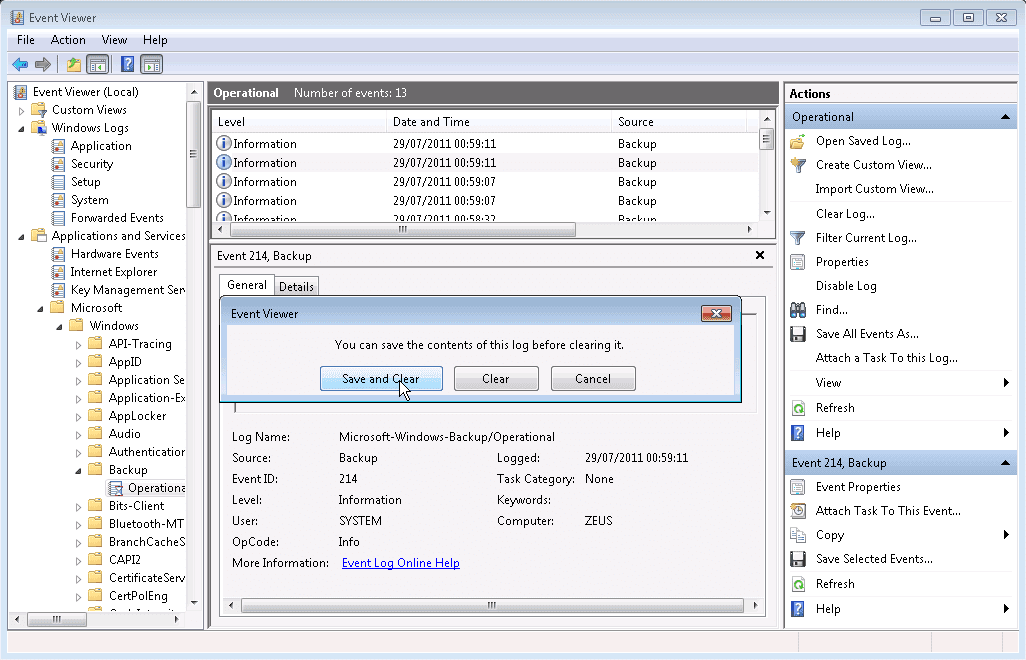
Clear Windows Server 2008 Backup Log
IDrive 174 BMR best practices for backup and recovery
What Methods To Be Followed For Data Backup And Data Recovery
Veeam Job Has Failed See Logs For Details Job Retro
CM Backup Review Cloud Service to Backup Contact SMS and Logs
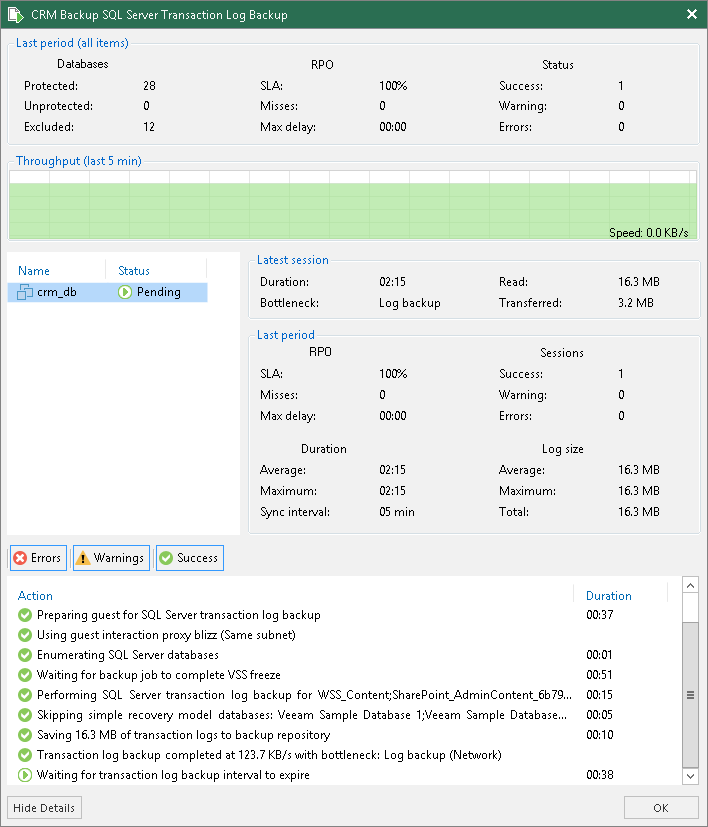
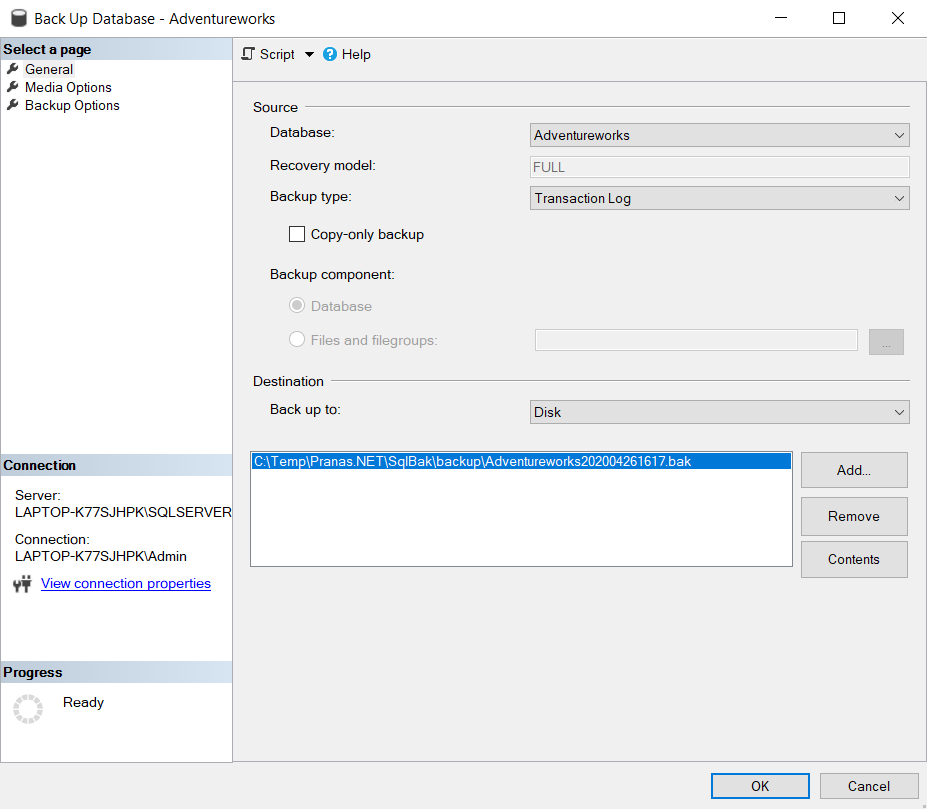
SQL Server Transaction Log Backups DB Authority
backup logs moodle3 6 Database
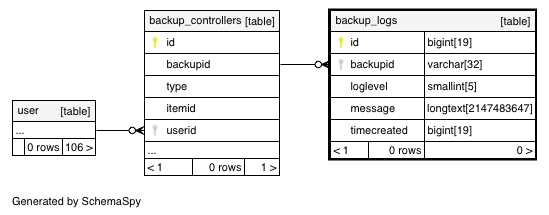
MongoDB Backup Comet Backup
Backing Up and Restoring Events
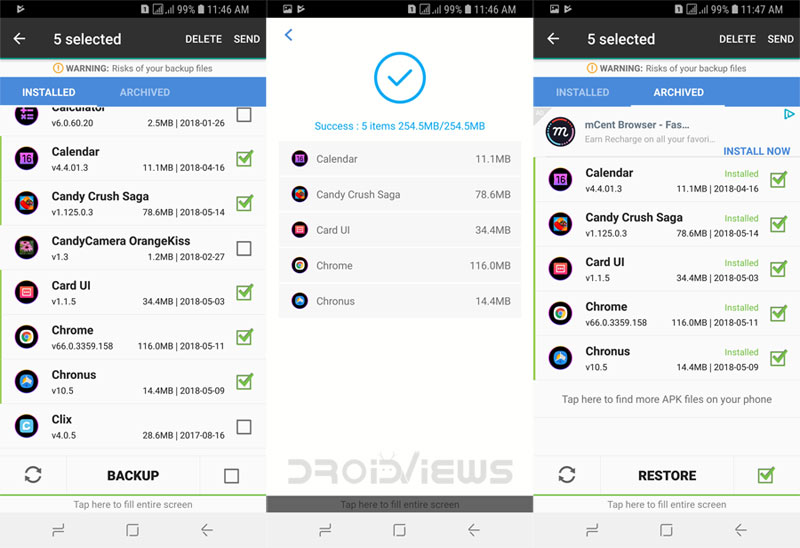
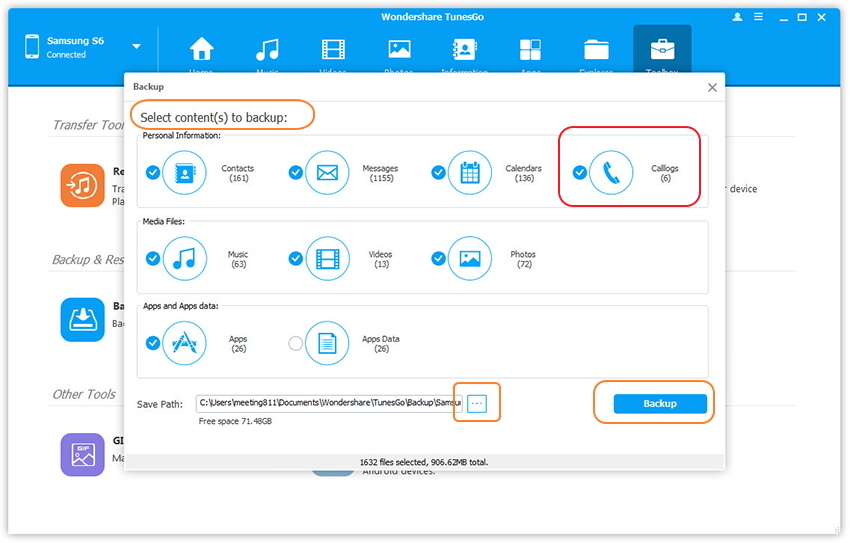
Backup Android Devices Apps Logs Contacts Messages amp Settings
Reason Behind Log Backup Failure But Full Backup Succession
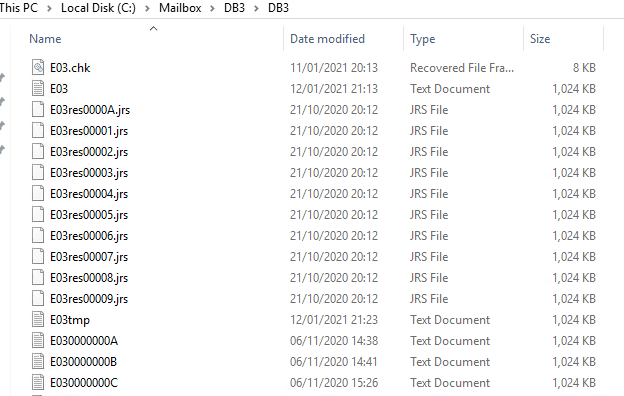
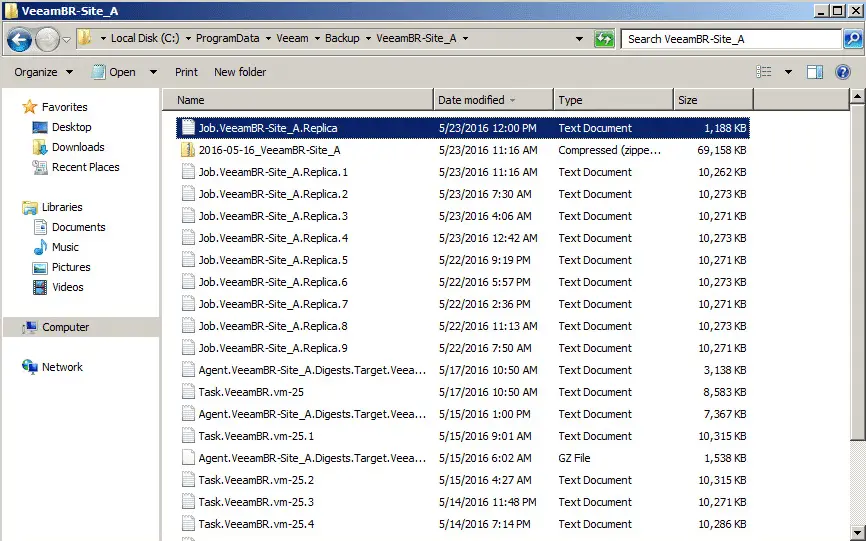
Backing Up and Restoring Raw Logs
Iphone Backup Browser fasrbasic
Back up my Aldebaran robot user data Aldebaran 2 4 3 28 r2 documentation
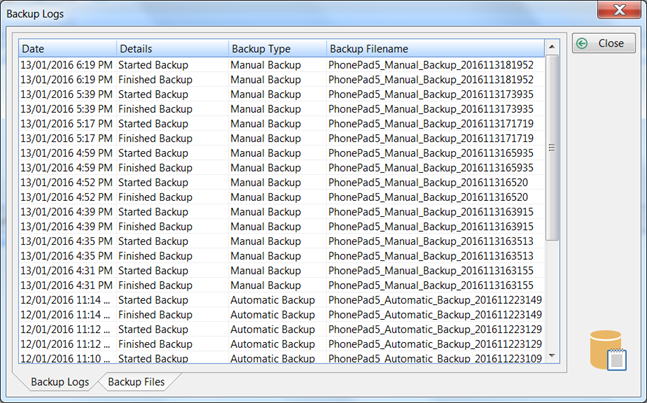
MiniTool ShadowMaker Logs View Detailed Backup Information
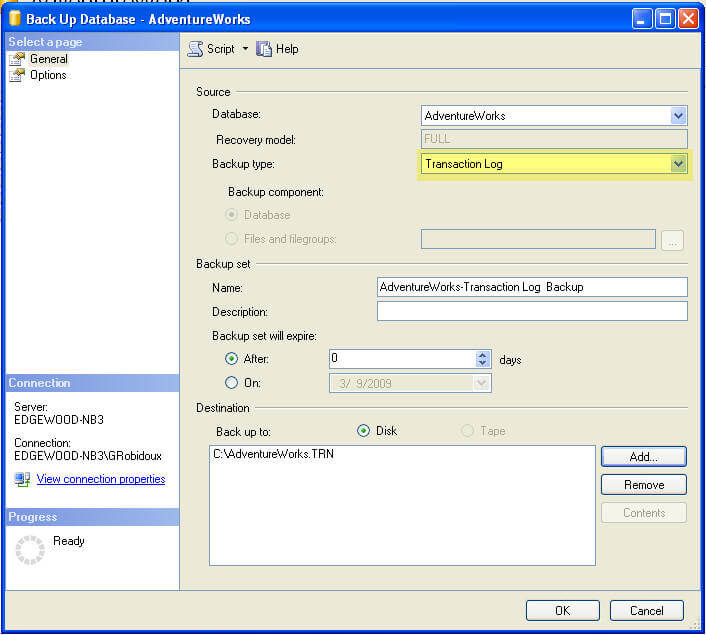
Transaction log backups in a SQL FILESTREAM database
Reason Behind Log Backup Failure But Full Backup Succession
Backing Up and Restoring Raw Logs
tape backup schedule spreadsheet template excelxo com
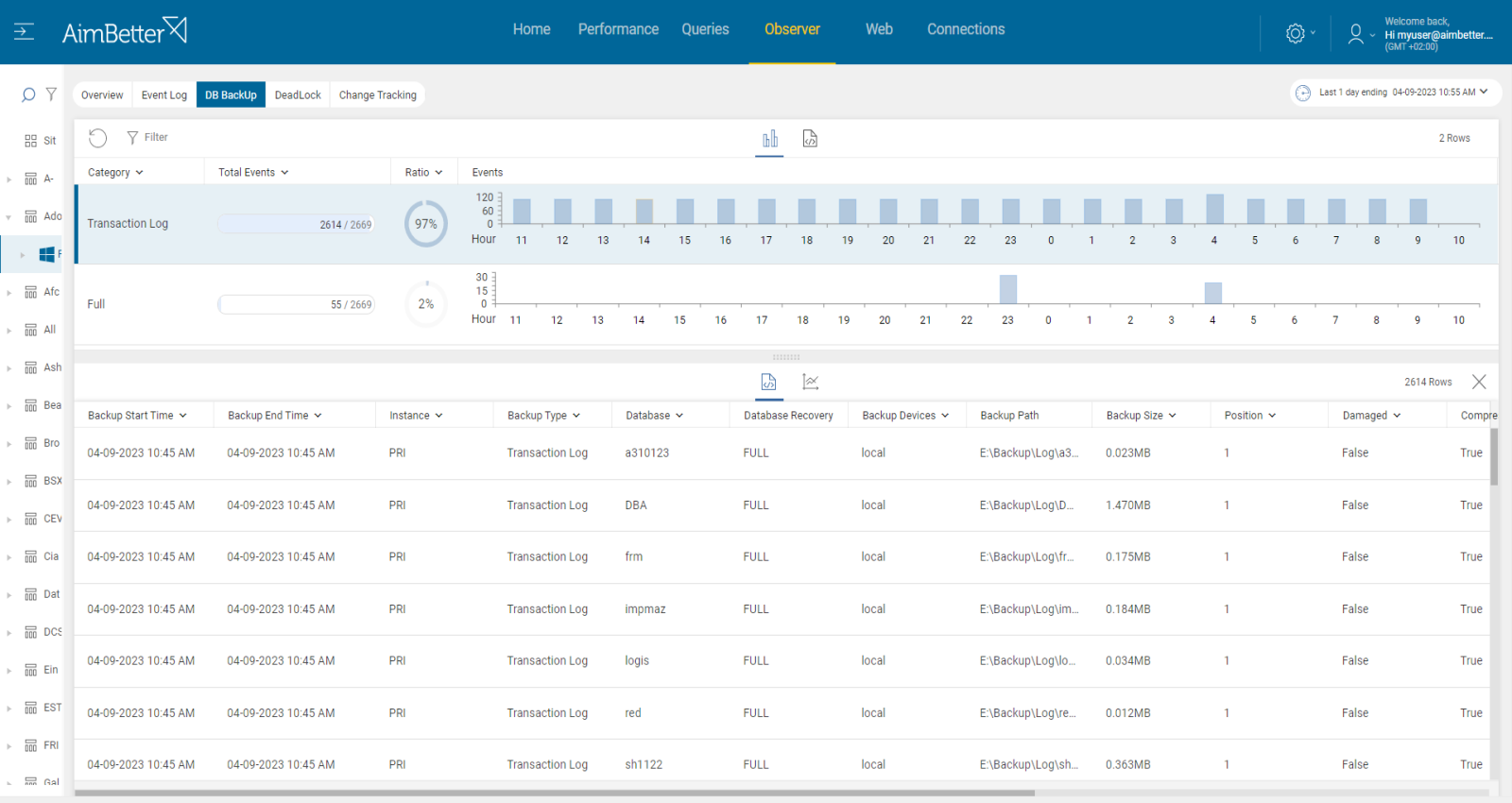
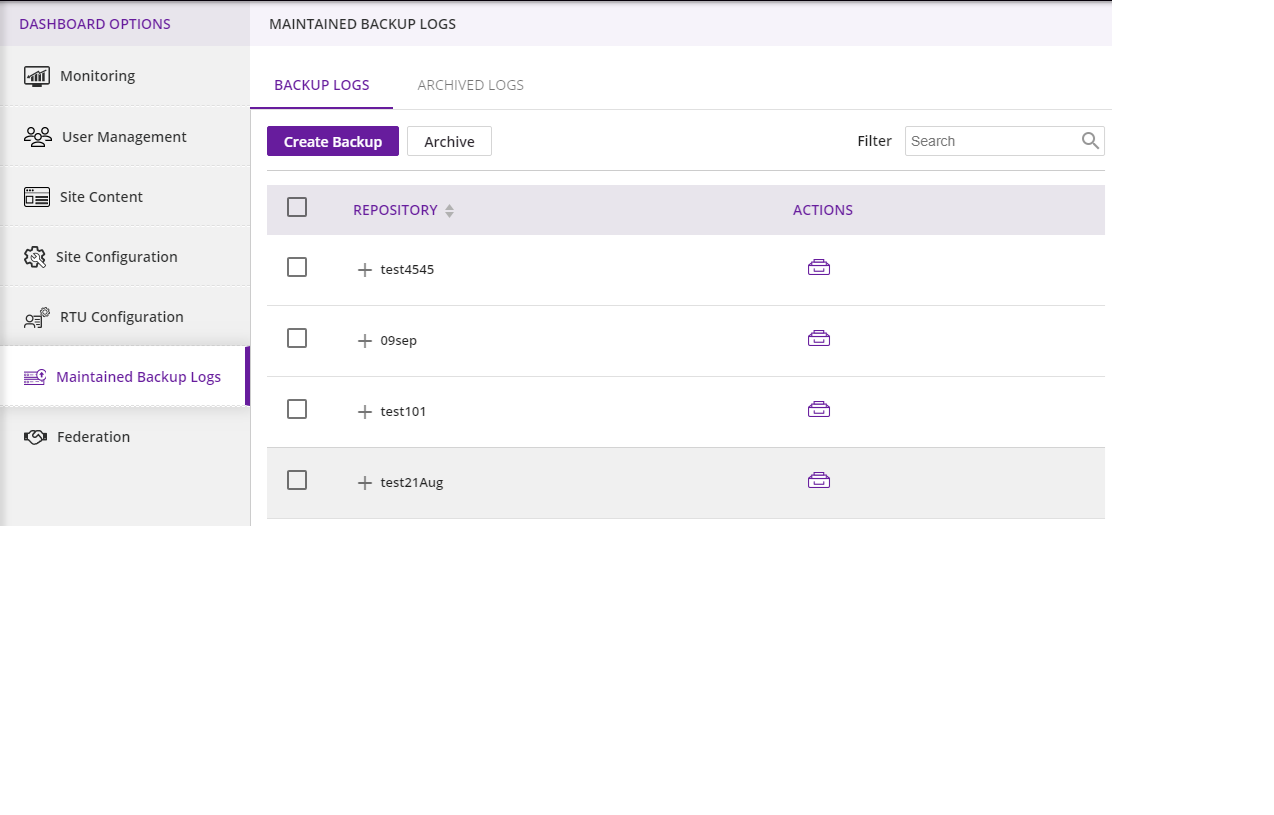
8 Maintained Backup Logs Acumos 1 0 documentation
Iphone Backup Browser fasrbasic
backup logs moodle3 6 Database
Back up my Aldebaran robot user data Aldebaran 2 4 3 28 r2 documentation
Create Synchronicity Backup and synchronization Features
MiniTool ShadowMaker Logs View Detailed Backup Information
Invalid Remote Certificate 8211 Veeam Backup 038 Replication
SQL Server Transaction Log Backup Best Practices
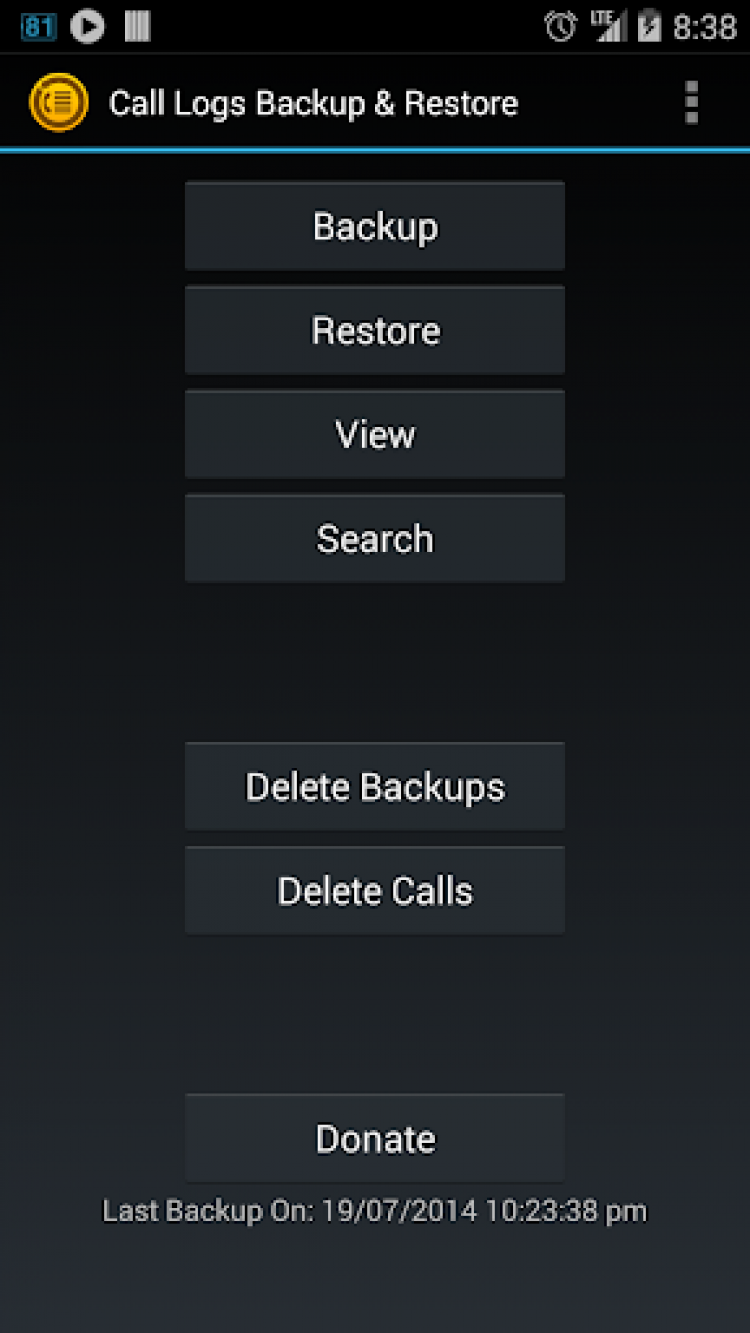
Call Logs Backup amp Restore c Android
Solved How to Backup Call Logs on iPhone
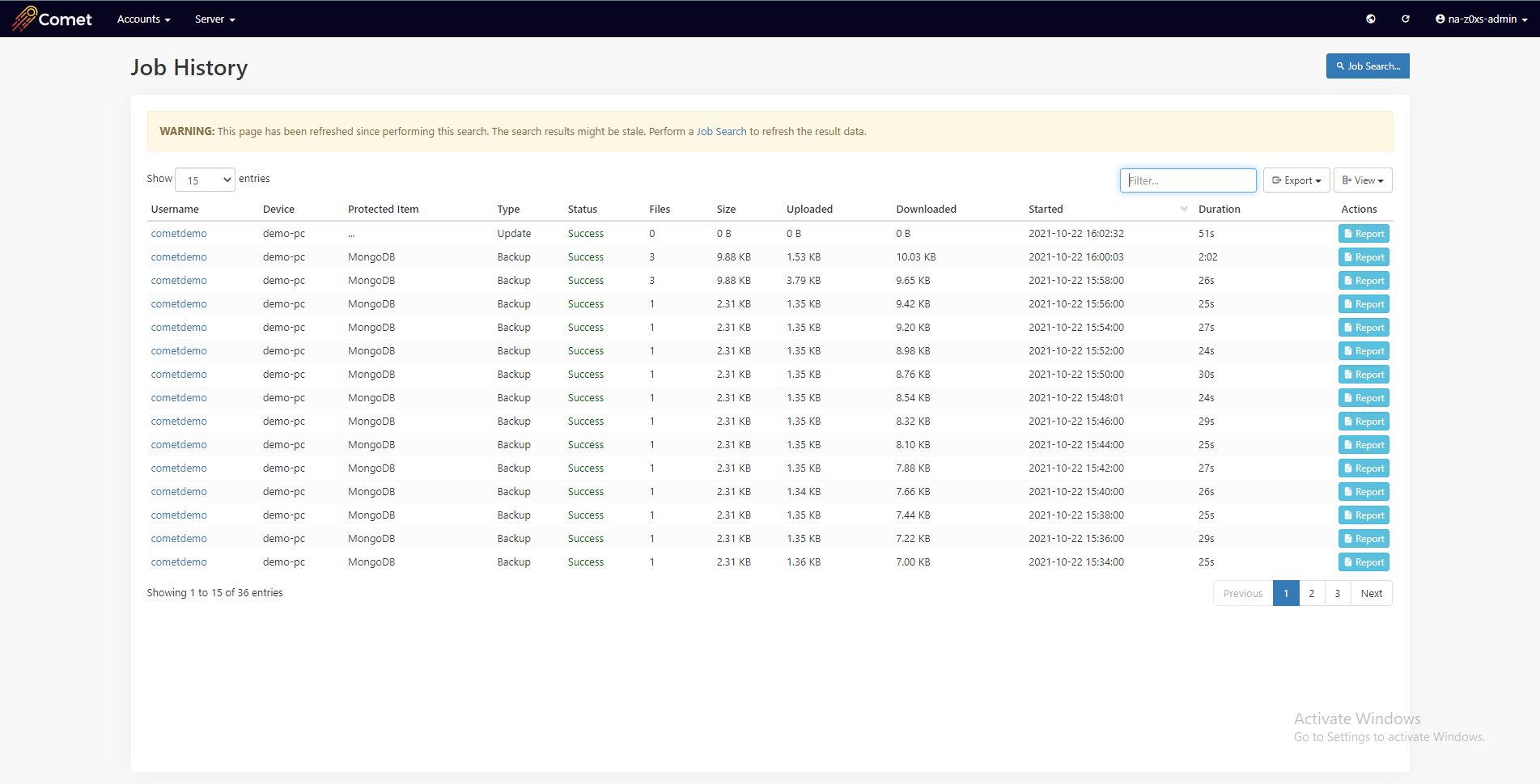
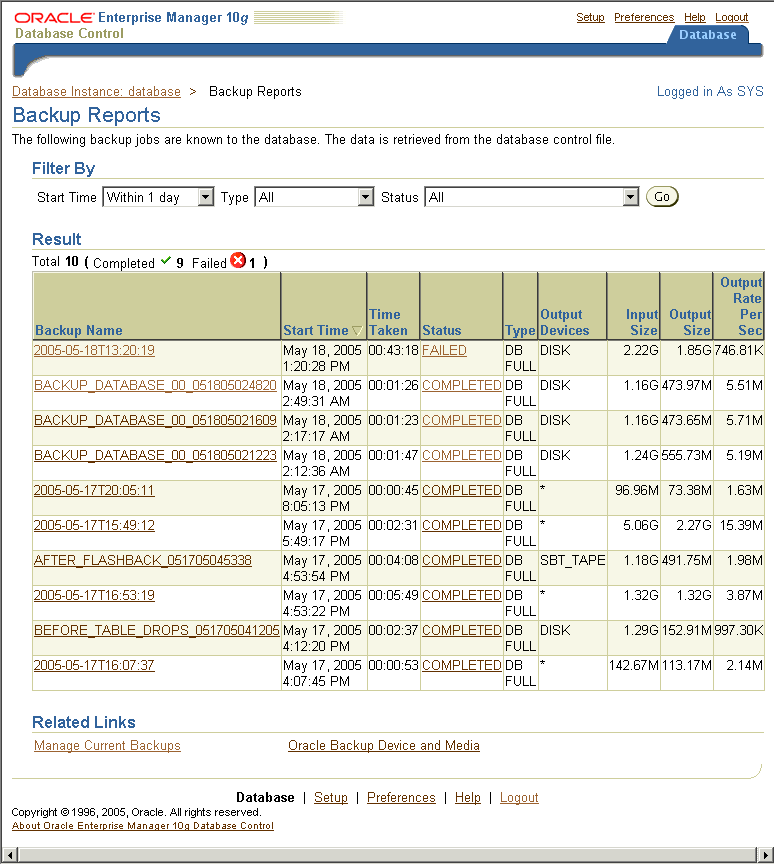
Displaying Backup Reports
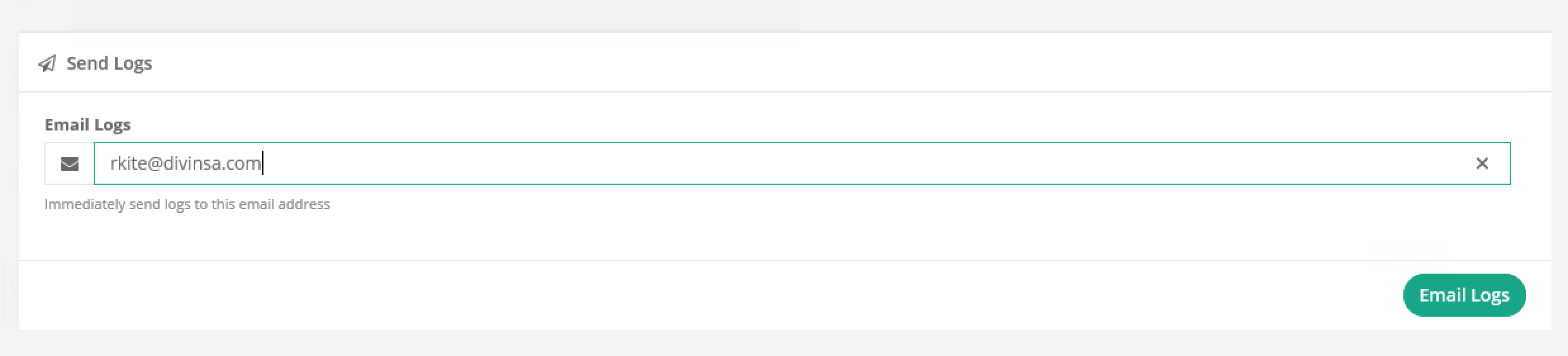
E Mailing Backup Status WholesaleBackup Knowledge Base
Backing Up and Restoring Microsoft Access Databases
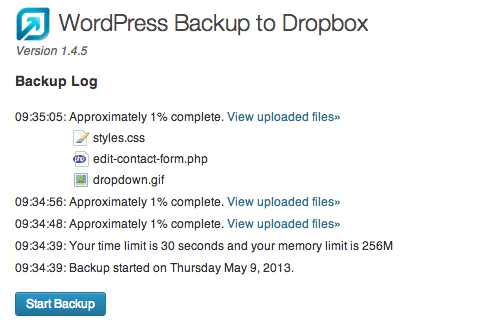
How To Backup WordPress To Dropbox For Peace Of Mind WPVKP
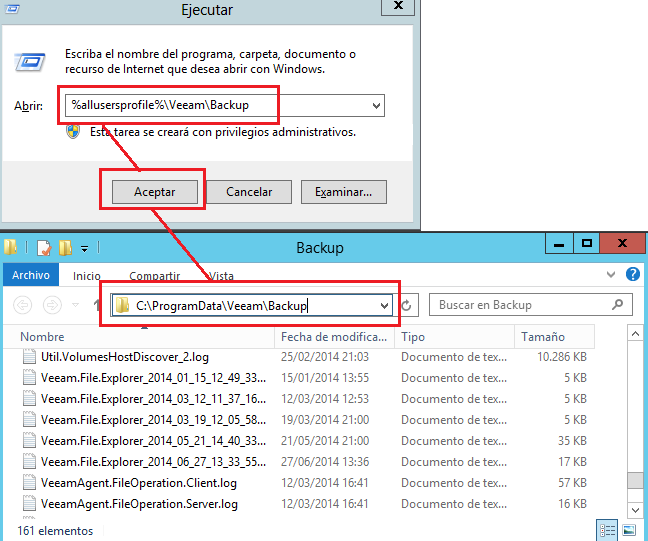
Veeam backup logs SYSADMIT
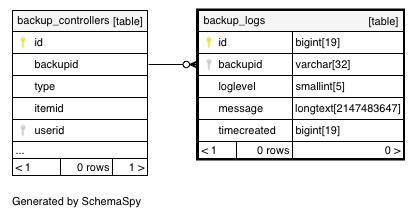
Backup Logs table backup logs Moodle LMS 3 9 Database schema
Verifying Scheduled Backups in Virtual TimeClock
Backup Messages Call logs Apps and More for Android APK Download
Why Transaction Log backups are important SqlBak Blog
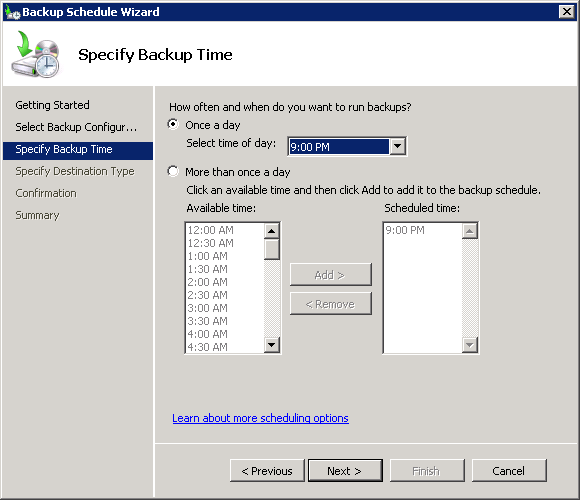
How to Schedule Windows Server Backup Practical365
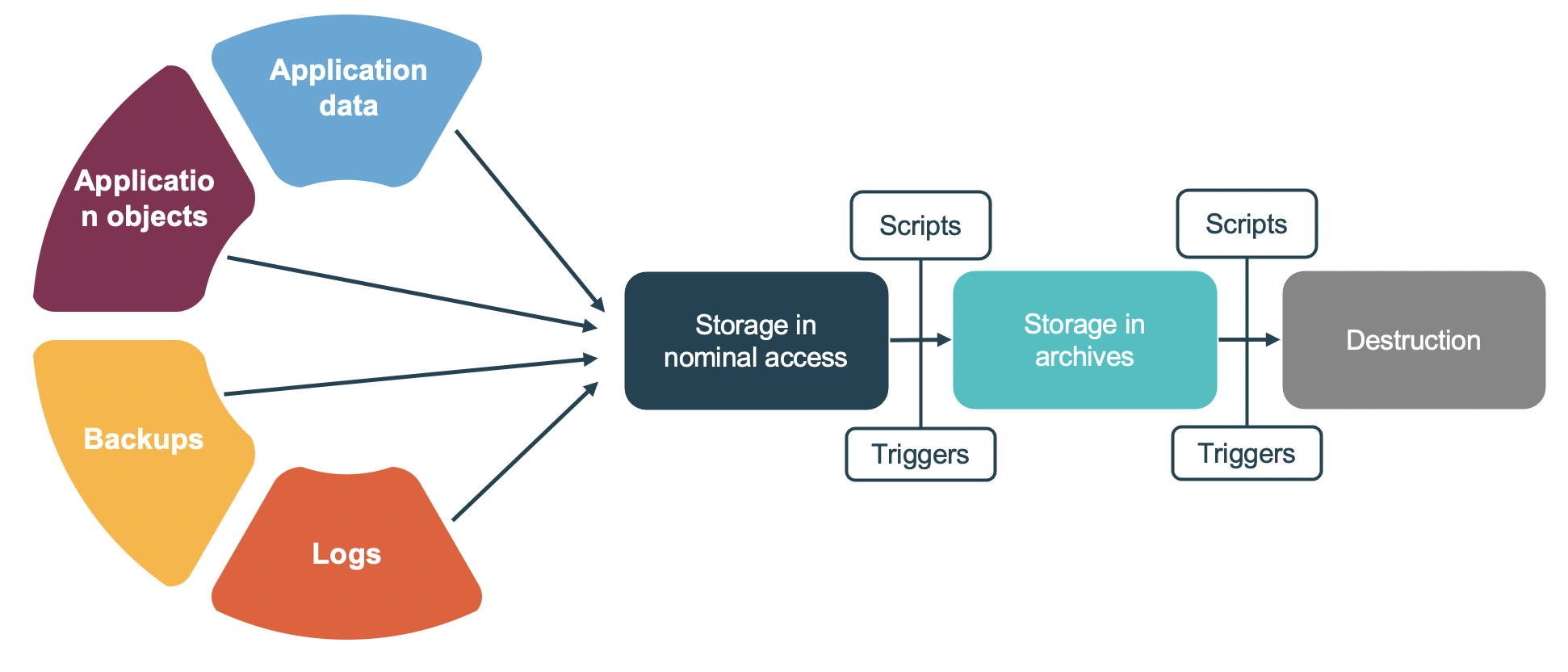
Data backup policy FinOps World
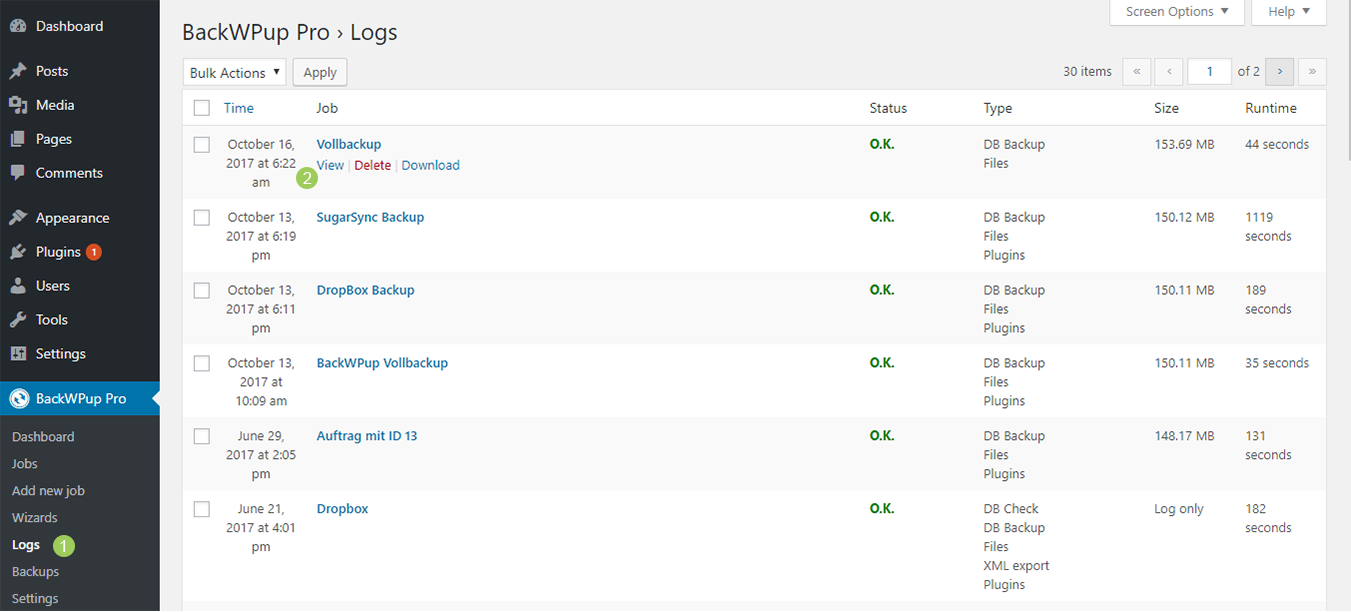
View the log of a backup job BackWPup Docs
Backup and Restore Android Call Logs How to Backup Android Call Logs
Difference between Full backup and Copy only full backup
The Backup Windows Plugin for LabTech
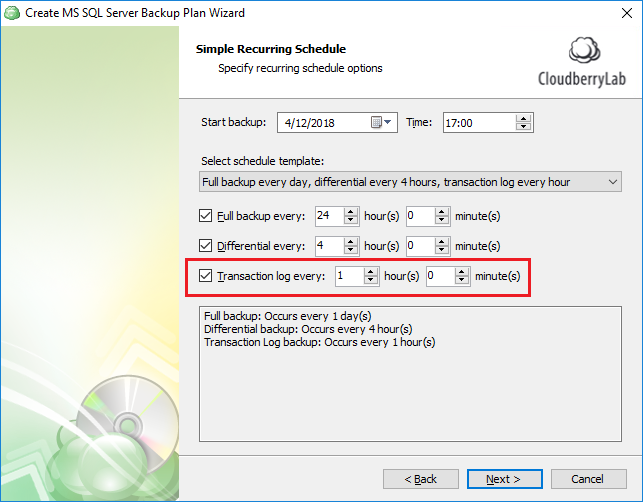
Transaction Logs Backup Improved in MSP360 Backup 5 7
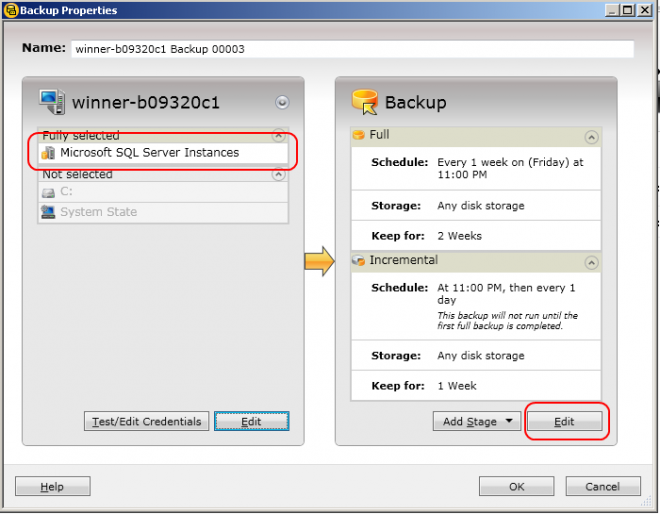
Backup copies creation and restoration Technical information
BRINGING BACKUP Video Log Thing YouTube
How to Transfer Call Logs from One Phone to Another
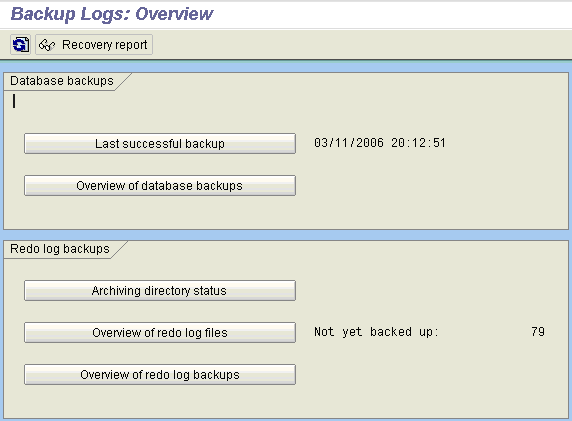
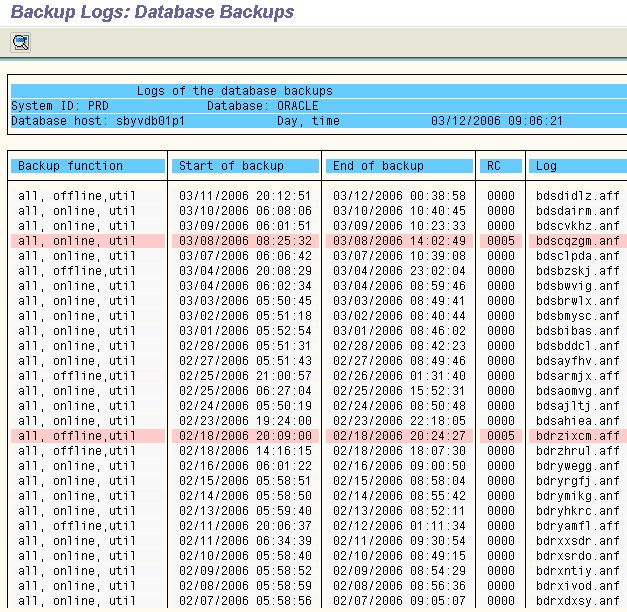
Backup Log Overview DB12 in SAP BASIS
Use Azure to backup on premises Files and folders Step by step Guide
How to Clear Exchange Logs files
MDL 37891 Course backup logs inaccurate Moodle Tracker
SQL SERVER FIX ERROR 4214 BACKUP LOG cannot be performed because
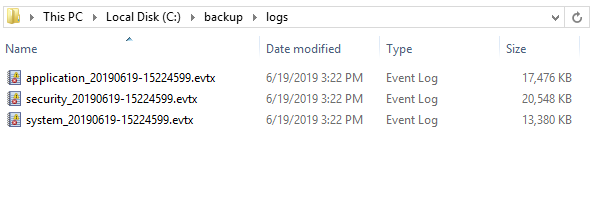
Batch Script to Automate Event Log Backup on Windows
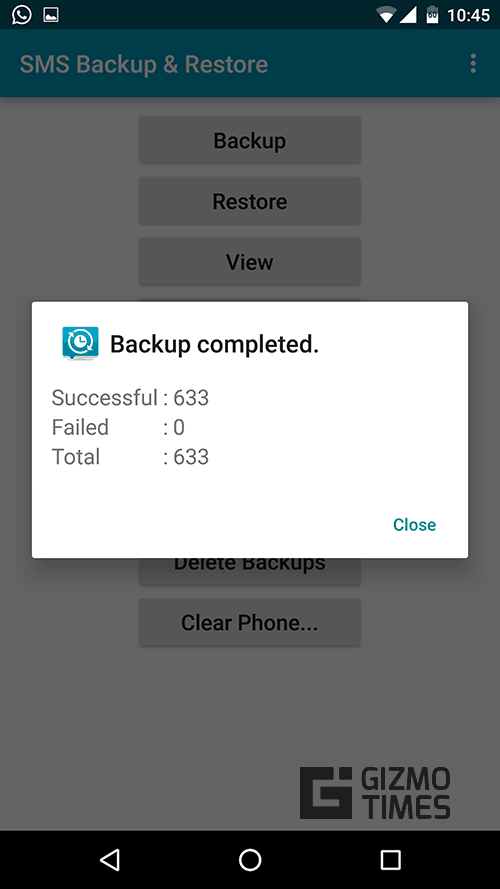
SMS Backup amp Restore Android Apps on Google Play
How to Create A System Image Windows 10
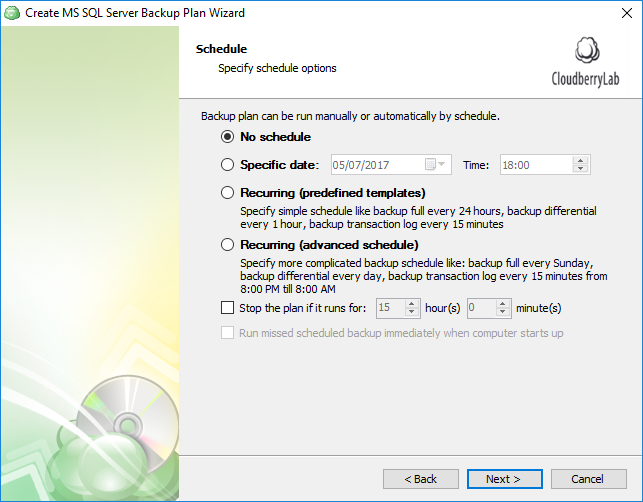
Backup and restore methods available for MS SQL server databases
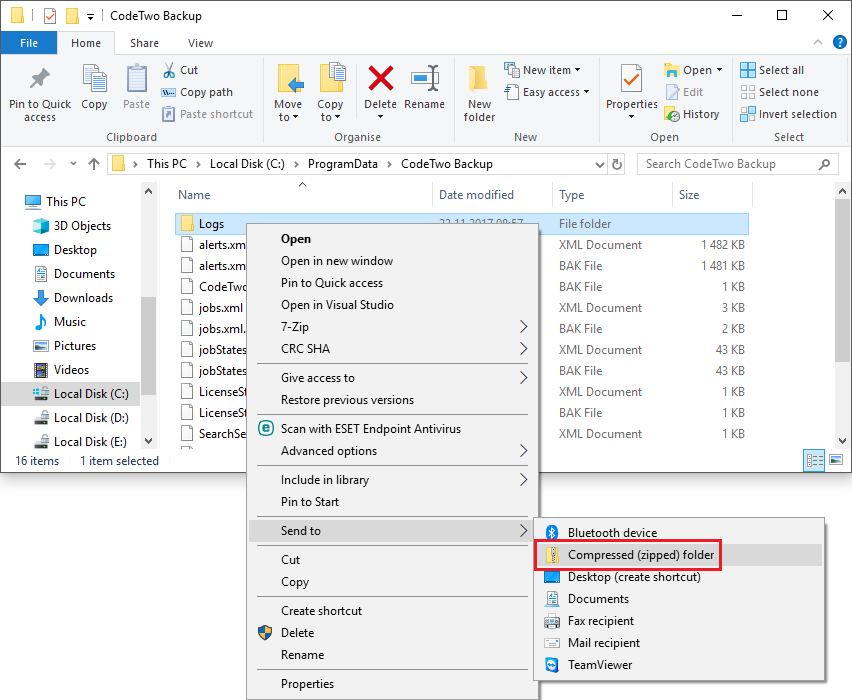
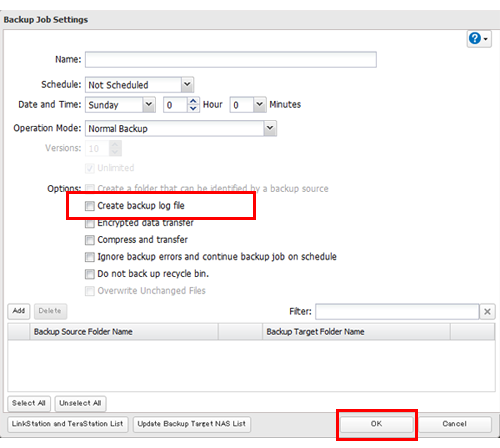
Monitoring and diagnostics Log files CodeTwo Backup User s manual
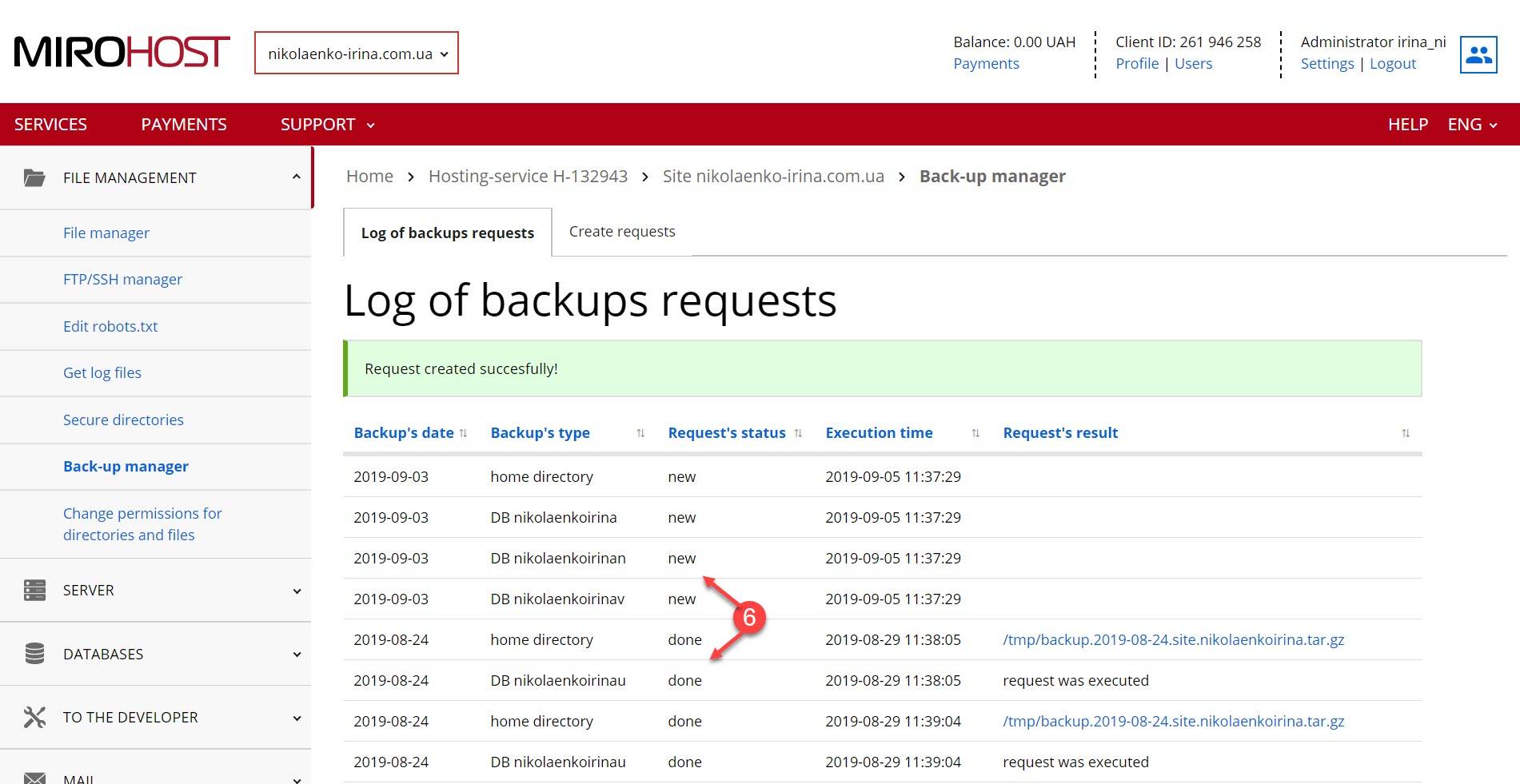
How to Obtain Backup Logs Details of an answer Buffalo Inc
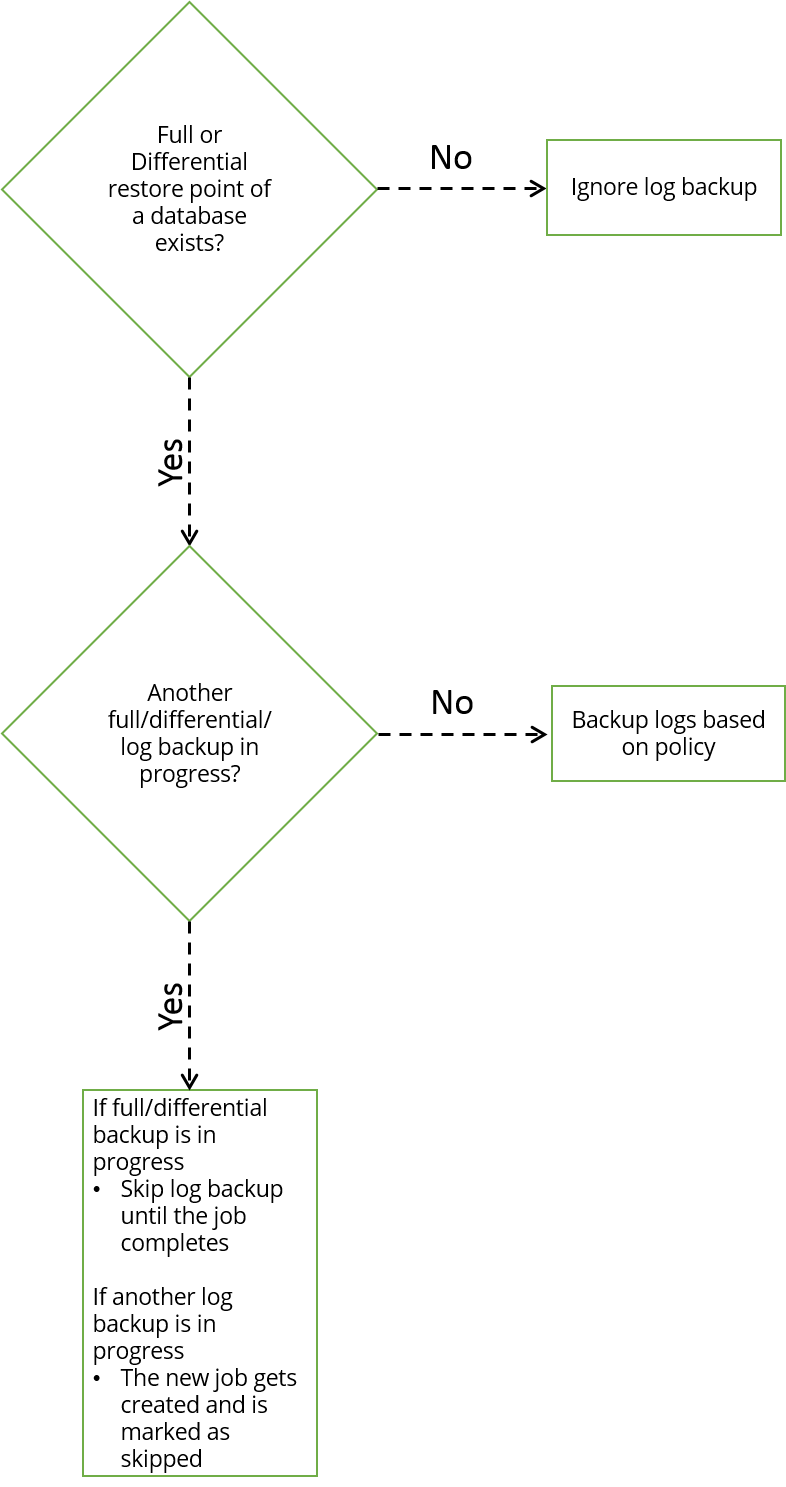
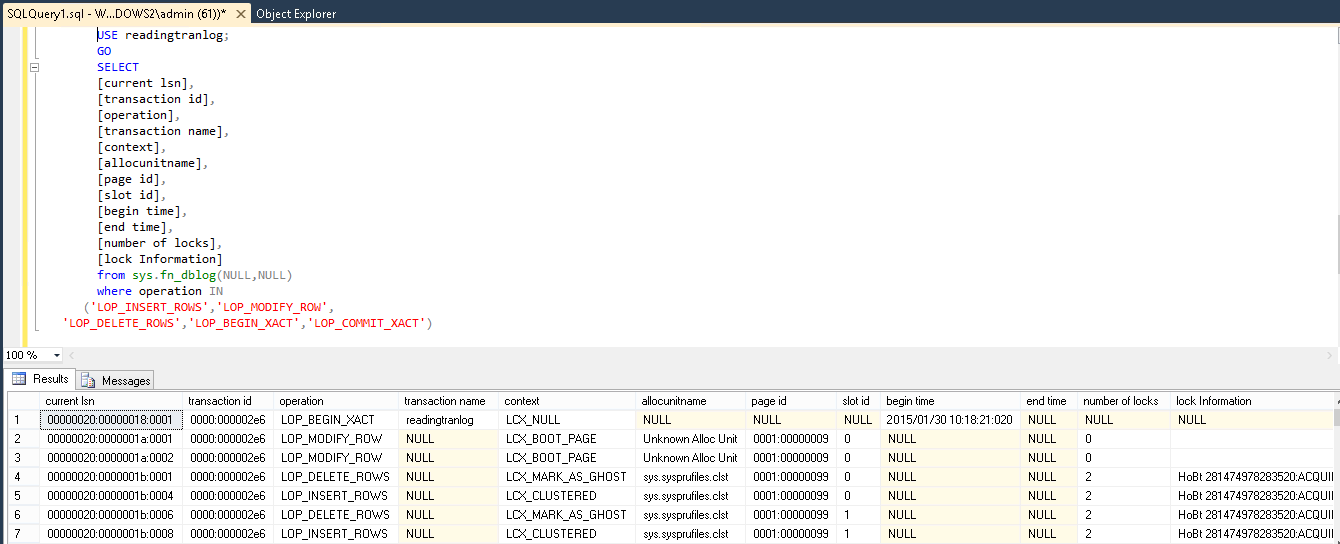
Simple Way of Reading SQL Server Transaction Logs
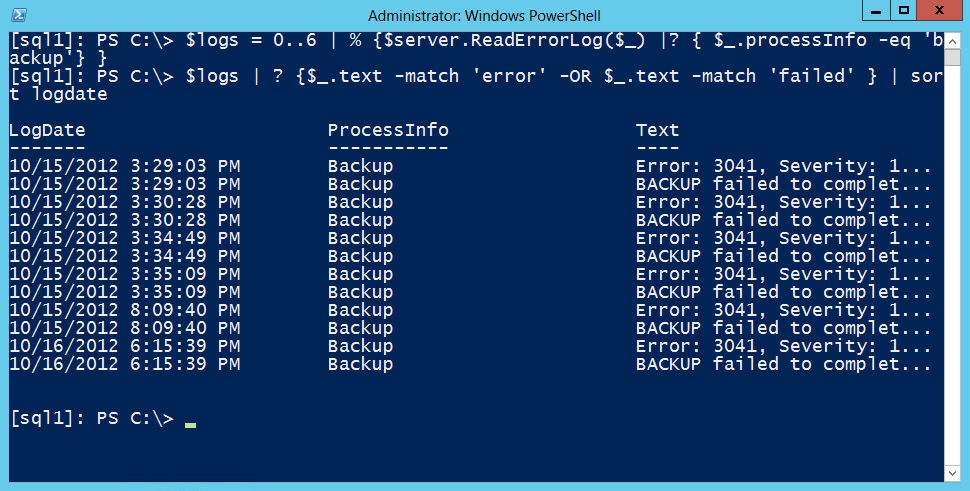
Use PowerShell to Parse SQL Server 2012 Error Logs Scripting Blog
Backup Log Checks and What They Can Tell You Rapid7 Blog
Eddie s Blog Configuring VCSA 6 5 Backup Lessons Learned
Oracle Database Commands and Practical Examples OEM 13c Schedule
Backup Call Logs amp Text Messages to Gmail
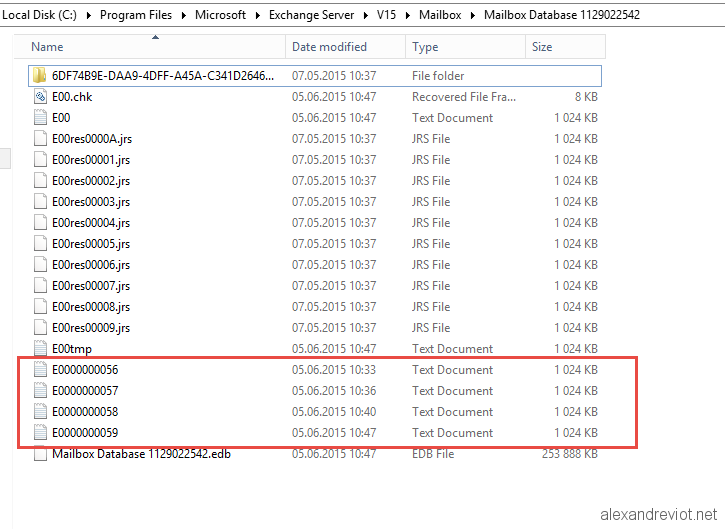
Exchange 2013 VSS backup does not clean logs 800423f3 Alexandre VIOT
Apply Archive Logs to Cold Backup Database E Business Suite and
Windows Backup error 0x81000019 Check VSS and SPP event logs Super
ITs Amazing IT Technical Support How to backup SQL logs and truncate
How Do I Backup Logs In Readable Format To Prevent Lz4 Decompression From Running - The pictures related to be able to How Do I Backup Logs In Readable Format To Prevent Lz4 Decompression From Running in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.
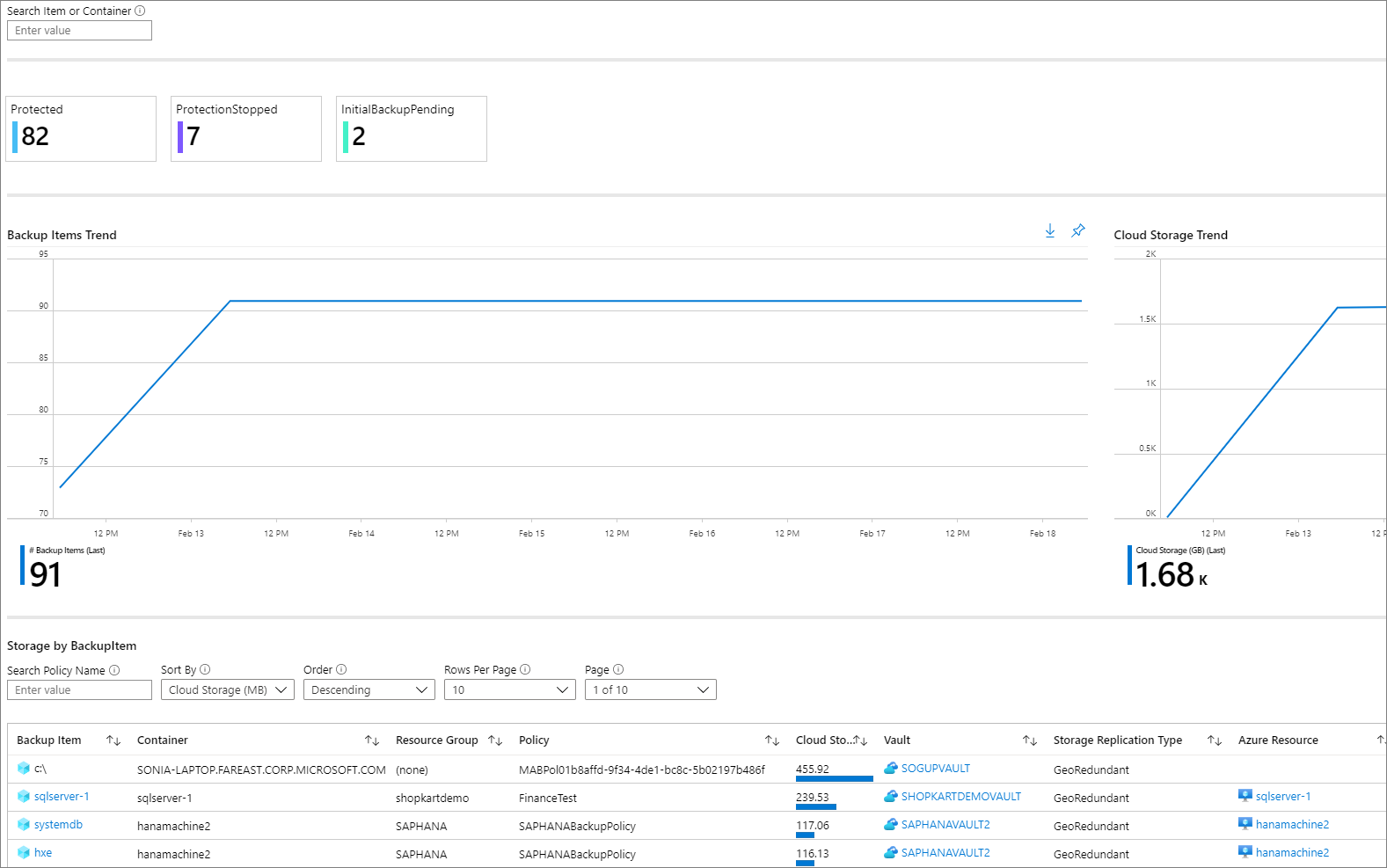

















/userfiles/Backup-Log-Overview-2.jpg)